OM Group’s ISSO spearheaded implementing the Army directed initiative regarding DoD’s Continuous Monitoring and Risk Scorecard (CMRS). This makes USACRC the first organization to implement the end to end continuous monitoring solution and successfully have that data reported into the enterprise Mission Assurance Support System (eMASS).
As a result, the USACRC will be a pilot program for updates and assist in efforts to synchronize CMRS and eMASS Army wide. All of which will streamline cyber monitoring, reduce security risk and conserve Army resources in the future. This will increase the Army’s success rate while fielding this solution enterprise wide.
OM Group applies a proactive approach to safeguarding a customer’s IT environment and data. Regardless where your AIS, Enclave, Platform IT, or outsourced service/information system resides in the System Life Cycle (SLC), or your system/security categorization, OM Group has trained and certified personnel to ensure you meet or exceed DoD and Federal compliance requirements.
In supporting DIACAP/RMF activities, our subject matter experts have the proper and current information assurance certifications to perform information assurance functions in accordance with DoD 8570.01-M, Information Assurance Workforce Improvement Program -- tailored to the appropriately assigned IAT level and Computing Environment (CE).
OM Group team ensures your software/application, web service, desktop application, IA Tool, or collaboration tool meets the requirements for a Certificate of Net worthiness (CoN). Our services include support for Government Off the Shelf (GOTS) and Commercial Off the Shelf (COTS) and spans the US Army, Army National Guard (ARNG), Army Reserve, DoD, and, Federal information systems.
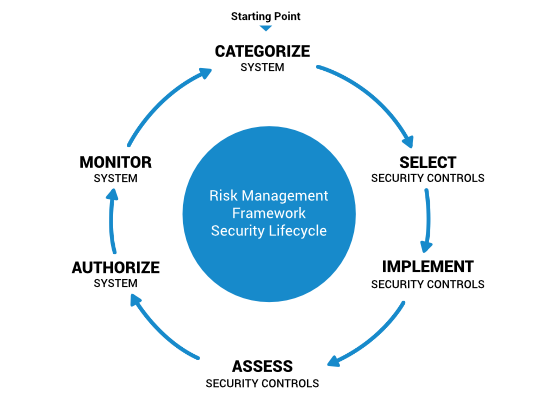
OM Group’s IA experts follow a code of practice for information security controls based on industry leading certification in ISO/IEC 27000:2016 for Security techniques -- information security management systems Our customers rely on our deep experience in trusted IT security tools and techniques to quickly assess current maturity levels, situation and needs. We implement metrics-based security solutions that will measurably improve your overall security posture. From our experience, RMF is more than just compliance – it’s about identifying and mitigating the impact to your mission if the non-compliant control is exploited, and preparing contingencies should the unexpected happen.
- NIST RMF SP 800-37 based IA controls implementation
- STIGs/Scans, Mitigating Support
- IATO/ATO Certification Support
- DR and COOP Exercise Support